The role that the payment terminal plays in the PCI-validated Point-to-Point Encryption (P2PE) process is crucial. The terminal is the first point of interaction (POI) with the credit or debit card – which is why you might hear or see the term “POI device” when a PCI P2PE solution is discussed. What sets a PCI-validated P2PE device apart from non-validated devices include the methods required to encrypt data, the tamper-resistance/responsiveness of the device, and the key injection of the devices.
The PCI P2PE Device – Requirements
Any device used in a PCI-validated P2PE solution, such as Bluefin’s solution, must also be validated and approved by the PCI SSC via the PCI PTS program with SRED (secure reading and exchange of data) listed as a “function provided” and with SRED enabled and active. Per the PCI SSC, SRED is:
“A set of PTS POI requirements that provide a standardized approach to protecting account data in POI devices. SRED requirements cover all methods of account-data entry supported by the POI device, and include physically and logically protecting account data within the device, protecting any associated sensitive data or functions, and providing for the encryption of account data before transmission outside the device.”
What sets validated devices apart from non-validated devices – aside from the fact that the devices must go through a rigorous review and certification process by PCI in order to be listed as PCI-validated P2PE devices – is that they encrypt payment data immediately upon swipe or dip, which prevents non-encrypted information from residing in the payment environment, even for one millisecond.
Think about that in the scheme of data breaches. A common tactic hackers use to steal credit card data is through point of sale (POS) memory-scraping malware, also called POS RAM scrapers. In a nutshell, POS RAM scrapers steal payment data from the RAM of POS systems. RAM scraper malware can reside on the payment terminal, finding clear-text card data in the milliseconds it takes a non-validated solution to encrypt the data, or it can be found in the RAM of the terminal.
Also, PCI-validated P2PE devices must have active tamper detection mechanisms to meet the physical security requirements of PCI PTS – which means that if malicious activity is detected, the device is automatically deactivated, preventing a breach at the POI device.
The Importance of Devices in the P2PE Solution
Whether you are a retailer, healthcare organization, educational institution or franchise – if you accept credit cards, you want to provide your customers the choice to pay anytime, anywhere. This is why device variety is very important to the P2PE solution. Bluefin currently has the largest list of PCI-validated P2PE devices of any P2PE solution provider – 28 – and we recently expanded our list with several new devices from Verifone, PAX, Ingenico and ID Tech, including the:
- Verifone MX 925, MX 915
- Ingenico iPP350, ISC Touch 250 and the ISC Touch 480
- PAX S300 and A920
- ID Tech Augusta S
Additionally, we added new Application Listings, including
- Ingenico RBA v1.1
- Ingenico RA1 v20.0x
- Verifone FormAgent/XPI v5300
The Importance of Chain of Custody in the P2PE Solution
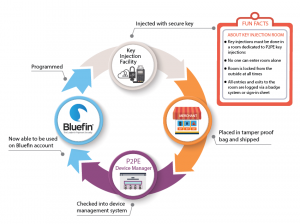 Just as important as the devices themselves is the device chain of custody required by PCI for validated P2PE solutions. As part of Bluefin’s PCI-validated P2PE solution package, we provide our partners and clients access to our patented online device management system. The P2PE Manager® allows Bluefin clients to monitor the complete lifecycle of a payment device. This includes key injection, device shipping and tracking for chain-of-custody, device state and attestation management, and a record of every decryption performed by every device, including the management of:
Just as important as the devices themselves is the device chain of custody required by PCI for validated P2PE solutions. As part of Bluefin’s PCI-validated P2PE solution package, we provide our partners and clients access to our patented online device management system. The P2PE Manager® allows Bluefin clients to monitor the complete lifecycle of a payment device. This includes key injection, device shipping and tracking for chain-of-custody, device state and attestation management, and a record of every decryption performed by every device, including the management of:
- Users, Partners, Clients, Locations
- Device Deployment, Activation, Termination (end of life)
- Device Shipping and Tracking (chain of custody)
- Transactional, Device and User History
- Device, Shipment, and Transactional Reports for Exporting/Download, as well as the P2PE Annual Audit
In addition to additional devices and applications, we also added several new Key Injection Facilities (KIFs) as part of our P2PE Component Provider list, including Secure Retail Limited and the Verifone KIF, bringing our total partner KIFs to 7.
PCI P2PE – No Longer “Just” a Solution
We recently celebrated our 4-year anniversary of PCI P2PE validation in March and we are excited that *most* of the industry now knows what P2PE stands for. It has taken a lot of education on the part of PCI, vendors like Bluefin, industry organizations, device manufacturers, and more for merchants and enterprises to understand the true value of a PCI-validated P2PE solution.
And now that the understanding is there, we see the industry moving more toward solutions that provide merchants and partners a “plug and play” approach to P2PE, where networks of providers and supporters will accompany PCI-validated P2PE solutions. Today, Bluefin’s Decryptx® partner network includes more than 70 processors, gateways and software providers, meaning that each of these companies offers Bluefin’s PCI P2PE solution through their own gateway, software or platform – making Bluefin’s PCI P2PE solution accessible to over 2M merchants in 24 countries. And now, with 28 devices and 7 KIFs, we are looking forward to taking P2PE to a global network level.
For more information on our P2PE solution, contact us.








