For any merchant that stores, processes and transmits payment and other sensitive cardholder data (CHD), PCI compliance requirements are not just another check-the-box organizational task. In fact, adhering to the rules and guidelines set by the PCI DSS (Payment Card Industry Data Security Standard) is both a regulatory requirement and also a vital component for securing sensitive data to protect against data breaches and card fraud.
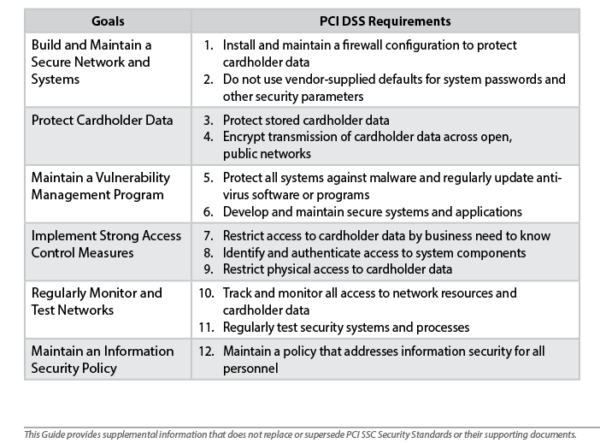 According to the PCI Security Standards Council (PCI SSC), PCI DSS is the global data security standard adopted by the payment card brands for all entities that process, store or transmit cardholder data and/or sensitive data. The standard – a PCI compliance checklist of 12 requirements – serve as best security practices to build, maintain and test vulnerabilities, access control measures and security policies that work in tandem to protect cardholder data and keep networks secure.
According to the PCI Security Standards Council (PCI SSC), PCI DSS is the global data security standard adopted by the payment card brands for all entities that process, store or transmit cardholder data and/or sensitive data. The standard – a PCI compliance checklist of 12 requirements – serve as best security practices to build, maintain and test vulnerabilities, access control measures and security policies that work in tandem to protect cardholder data and keep networks secure.
Despite its importance, achieving and maintaining PCI compliance isn’t always easy. Data breaches due to non-compliance with PCI DSS continue to be a significant issue, particularly as these standards become increasingly stringent.
A common theme among recent breaches is that organizations suffering these incidents were either not fully compliant or had fallen out of compliance with PCI DSS.
For example, the Verizon 2024 Data Breach Investigations Report highlights that many organizations fall out of PCI compliance soon after achieving it. In fact, fewer than one-third of breached companies were fully PCI-compliant when incidents occurred, often due to lapses in areas like multi-factor authentication and data encryption, which are essential for protecting payment information.
Let’s talk more about data encryption. The PCI DSS specifies how cardholder data should be protected, both in transit and at rest. This involves using strong encryption and limiting data storage to only what is necessary. PCI Security Standards Council recommends using both PCI-validated Point-to-Point Encryption (P2PE) and tokenization as part of a robust security strategy for protecting cardholder data.
P2PE encrypts cardholder data in transit – from the moment of capture at the point of sale (e.g., when a card is swiped, dipped, or tapped) until it reaches a secure endpoint. Tokenization protects data at rest, removing sensitive information from your internal system — where it’s vulnerable to hackers — and replacing it with a one-of-a-kind token that is unreadable, even if hackers manage to breach your systems.
While many PCI DSS requirements function to keep data and networks secure from bad actors, cyber threats or even human error – a defending the fort type of strategy – P2PE and tokenization devalue sensitive data, rendering it useless in the event of a breach or insecure network. Together, P2PE and tokenization reduce the scope of PCI DSS requirements for merchants, supports compliance with specific PCI DSS requirements, and lowers the risk of data breaches.
Tokenization – Protecting PHI and PII Data
Speaking of data breaches, data has grown in value, and cyber thieves are now cashing in on stealing personal identifiable information (PII) and personal health information (PHI), selling off the data in pieces on the dark web. This type of data has a longer shelf life for cyber thieves and is used for malicious activities such as identity theft and medical fraud.
While the average cost of a data breach reached $4.5 million in 2024, healthcare breach costs soared to $10.9 million per incident – largely due to the sheer amount of PHI, PII and payment data being processed.
As data breach costs continue to rise, so does vulnerability of customer data. In 2024, ransomware and extortion tactics were a dominant threat to organizations, accounting for 30% of all breaches and reflecting a shift towards attacks that involve holding data hostage for financial gain. – Verizon’s 2024 DBIR
The state of data breaches and its after-effects from stolen payment, PHI and PII data is where tokenization comes into play. Historically, tokenization has been deployed to protect credit card and debit card data in storage, but in recent years, tokenization has been expanded to now also “mask” Personally Identifiable Information (PII), Protected Health Information (PHI) and banking information, securing data such as:
- A real name or alias, signature, or physical characteristics or description
- Postal address or telephone number
- Unique personal identifier, account name, address, or email address
- Education and employment, including employment history
- Social security number, driver’s license number or passport number
- Medical or health insurance information
- Bank account number, credit/debit card number or any other financial information
How Does Tokenization Apply to PCI DSS Standards?
PCI compliance with tokenization addresses PCI DSS requirement #3, protecting cardholder data at rest. It satisfies this critical requirement by eliminating stored CHD from as many systems as possible. Credit card tokenization not only replaces sensitive data, but it also minimizes the amount of data an organization needs to keep on file, which ultimately helps to reduce the cost of compliance with industry standards and government regulations, providing:
- Enhanced data security
- Reduced compliance costs
- Lower financial risks
- Increased customer trust
- Strong brand reputation
Bluefins ShieldConex®, Tokenization Solution
Bluefin specializes in payment and data security solutions to organizations, providing PCI-validated point-to-point encryption (P2PE) solution for the protection of point-of-sale cardholder data and ShieldConex®, a vaultess tokenization platform for the online protection of PII, PHI and financial data. Combined, P2PE and ShieldConex provide the most secure and holistic solution for retail payment and data security – devaluing all data in the event of a breach.
Choosing Bluefin for tokenization means you get:
- PHI, PII and payment data protection
- Minimized PCI footprint
- Retail Orchestration – the ability switch payment partners at will
- Vaultless tokenization, which means you own your own data
- 120+ validated P2PE devices and 27 Key Injection Facilities – that’s 10x more than our competitors
Want to learn how ShieldConex can work for your organization? Learn more and contact us today.








