What is SSL/TLS?
Transport Layer Security (TLS) is a cryptographic protocol used to establish a secure communications channel between two systems and was preceded by Secure Socket Layer (SSL). It is used to authenticate one or both systems and protect the confidentiality and integrity of information that passes between systems.
Flaws have been discovered in TLS 1.0, so the Payment Card Industry (PCI) Council has listed TLS 1.0 as an insecure method to use for secure transactions.
PCI has established a date of June 30, 2018 for all payment processors, merchants and vendors to upgrade to a secure version of TLS (1.1 or higher).
Note that as a software provider and/or merchant, you have an established TLS connection with Bluefin to communicate with our PayConex gateway to process your customers’ payments. In order to continue this communication, we must have all providers and merchants update to TLS 1.2 immediately.
The reason why we are mandating upgrade to 1.2 and not 1.1 is that 1.1 will soon be obsolete. You will avoid two integrations (one to 1.1 and then another to 1.2) by just updating to 1.2 now.
Get more information on TLS 1.2.
What is the difference between SSL and TLS?
SSL is a security protocol that uses cryptographic connections to establish authentic, and secure communication between a network of computers. TLS is also a security protocol that ensures that data that is delivered over the internet remains secure, protecting sensitive data from malware and hackers.
What are the SSL/TLS vulnerabilities?
Because of its widespread use online, SSL and TLS have been targets by security researchers and attackers. Many vulnerabilities in SSL and TLS have been uncovered over the past 20 years.
What are the impacts of vulnerabilities?
If a vulnerability is exploited through harmful cyberattacks, the impact of such exploitation could cause severe repercussions and could compromise personal, sensitive data. Examples of vulnerabilities are listed below:
- Loss of confidentiality or integrity: Many of the attacks, particularly protocol vulnerabilities, allow for Man-in-the-Middle attacks allowing an attacker to decrypt sensitive information.
- Loss of cryptographic keys: In some of the most serious cases, vulnerabilities could allow an attack to steal long-lived cryptographic keys.
How to avoid SSL/TLS vulnerability?
Avoid SSL/TLS vulnerability by migrating to TLS 1.2. Bluefin requires that you have TLS 1.2 in place by May 15th, 2018.
Also, our CERT environment ONLY supports TLS 1.2 at this time. Thus, you can use this environment to test if your solution is TLS 1.2 compliant. If it is not, you will get a connection error.
How do I migrate to TLS 1.2?
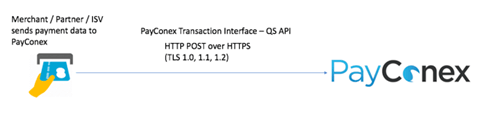
Our customers that integrate into PayConex do so through the QSAPI (PayConex Application Programming Interface/API) interface that uses encryption (HTTPS – TLS 1.0, 1.1, 1.2) for the HTTP POST method (how the data is submitted). A diagram of this flow is below.
How your organization migrates to TLS 1.2 depends on how you chose to integrate with PayConex via our QSAPI API.
Additionally, the PCI Council provides guidance on how to begin the migration process.
- Identify all system components and data flows relying on and/or supporting the vulnerable protocols
- For each system component or data flow, identify the business and/or technical need for using the vulnerable protocol
- Immediately remove or disable all instances of vulnerable protocols that do not have a supporting business or technical need
- Identify technologies to replace the vulnerable protocols and document secure configurations to be implemented
- Document a migration project plan outlining steps and timeframes for updates
- Implement risk reduction controls to help reduce susceptibility to known exploits until the vulnerable protocols are removed from the environment
- Perform migrations and follow change control procedures to ensure system updates are tested and authorized
- Update system configuration standards as migrations to new protocols are completed
It is important to build a communications element into migration planning. Consider how much leg work it will take to get agreement on changing.
For additional FAQ’s, please visit the PCI Council’s website.
If you have other questions, please contact your Bluefin Relationship Manager.