ShieldConex®
Payment and Data Tokenization
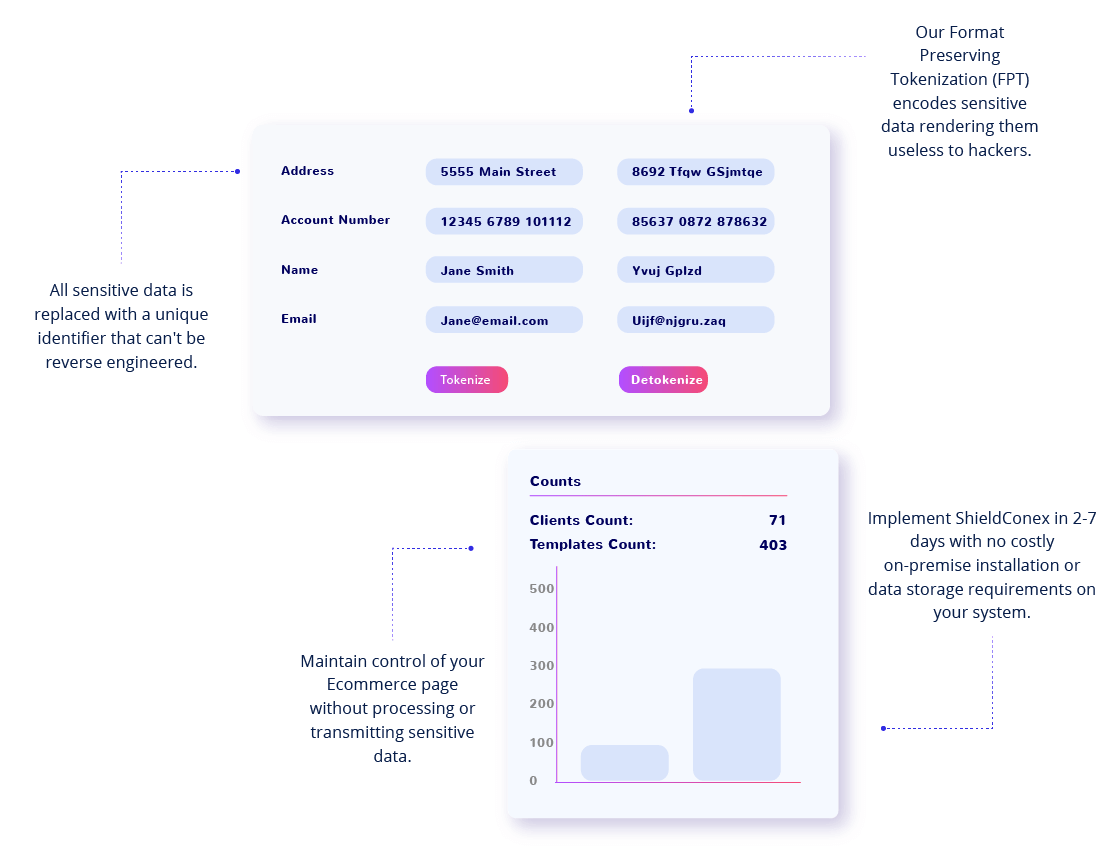
Tokenization masks data at the time of input and helps your organization meet evolving security standards. The ShieldConex platform provides vaultless, format preserving tokenization for every data element.
Tokenization masks data at the time of input and helps your organization meet evolving security standards. The ShieldConex platform provides vaultless, format preserving tokenization for every data element.
More personal, financial and health information is being entered online than ever before. Tokenization upon intake of payments and sensitive information ensures that all data is masked before ever reaching your system or network for processing and storage – securing your customer data in the event of a breach while meeting PCI DSS, Nacha, HIPPA, GDPR and CCPA regulations and standards.
Historically, tokenization has been deployed to protect credit card and debit card data in storage. Storing this data is essential for recurring and subscription transactions so that the customer can be billed on a regular basis without having to re-enter their information. Storing clear-text credit and debit card data in any form violates PCI compliance rules, as well as data privacy rules.
In recent years, tokenization has been expanded to now also “mask” Personally Identifiable Information (PII), Protected Health Information (PHI) and banking information, especially pertaining to ACH account details. Examples of the type of data a tokenization system can secure include:
Additionally, tokenization is no longer exclusively used for protection of data in storage. It can also be used to immediately tokenize data upon entry into a web form or Ecommerce page.
Digital tokenization has been around for over 20 years and was primarily designed to secure credit and debit cards. In the early days of digital payments, merchants and payment processors would store Primary Account Numbers (PANs) – the 16-digit debit/credit card number – alongside other transaction information. Because this sensitive payment information was stored in clear text, it was visible to anyone with system access and especially vulnerable to data breaches and theft. Inspired by physical token systems like casino chips and vouchers, digital tokens were created to substitute sensitive data in storage.
Any organization that accepts credit or debit card payments is required to keep that data as safe and secure as possible. The Payment Card Industry (PCI) Data Security Standard (DSS) is the set of regulations established by credit card companies to help protect payment information and are mandated by the credit card companies to ensure the security of credit card transactions.
Tokenization addresses PCI DSS requirement set #3: protecting cardholder data (CHD) at rest. PCI DSS seeks to reduce retention of sensitive data and safely govern its storage and deletion. Tokenization satisfies this critical requirement by eliminating stored CHD from as many systems as possible. Credit card tokenization not only replaces sensitive data, but it also minimizes the amount of data an organization needs to keep on file, which ultimately helps to reduce the cost of compliance with industry standards and government regulations.
Additionally, the responsibility to protect stored CHD and maintain the proper level of PCI DSS certification then falls on the token (solution) provider, so it ultimately reduces the cost of PCI compliance. This makes an especially big difference for organizations that want to support card-on-file or recurring payments.
To learn more, see our article Tokenization, Cardholder Data and PCI Compliance: What you Need to Know.
While data privacy regulations do not mandate the type of technology adopted to secure data, they both discuss pseudonymization and encryption as relevant data security measures.
One reason for tokens’ increasing use for sensitive, personal information is that they are versatile – they can be engineered to preserve the length and format of the data that was tokenized. Tokens can also be generated to preserve specific parts of the original data values; by adapting to the formats of conventional databases and applications, tokens can eliminate the need to change the database scheme or business processes. Organizations can treat tokens as if they were the actual data strings.
To learn more, read our article Understanding PHI, PII, Data Privacy & Tokenization.
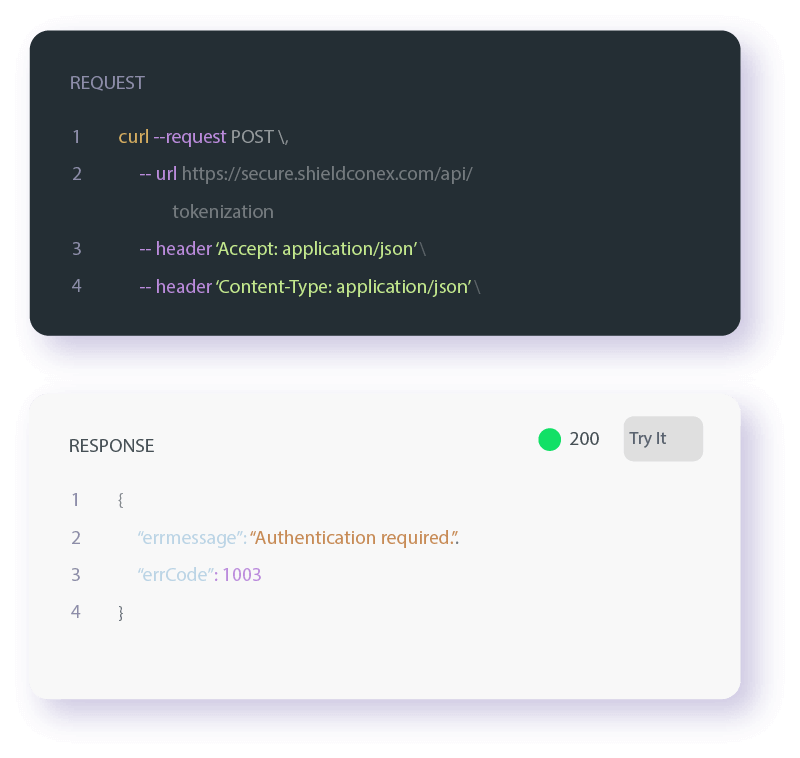
ShieldConex is an entirely cloud-based product that leverages APIs and secure iFrames configured through our ShieldConex Manager administration portal. Bluefin will provide access to the ShieldConex APIs, login credentials to ShieldConex Manager, and online integration documentation. We also provide integration assistance as needed to get your organization live with ShieldConex in a timely and successful manner.
Learn more about our API and iFrame implementation options.
"*" indicates required fields

