Today’s consumers are used to various payment options. Mobile apps, digital wallets, tapping or dipping chipped credit and debit cards are all common practice. So, when faced with the option of using the magnetic stripe on a card for payment, it feels antiquated, less secure. The adoption of EMV – and the shift of liability from credit card companies to merchants in cases of fraudulent point-of-sale transactions with EMV cards – can take credit for that “not-so-safe” feeling.
Back in the early 1990s, it became clear to fraudsters that card data could easily be read from a magnetic stripe card and then duplicated to create another (counterfeit) magnetic card. The most common form of fraud was card skimming, where criminals would use small, handheld devices to steal credit card information from unsuspecting customers. As a response to the increasing problem of fraud in the payment card industry, the development of the EMV standard began.
EMV stands for Europay, Mastercard, and Visa and is a global standard for credit card processing and security created to protect customers and merchants from fraud.
In 1994, the first version of the EMV standard was released, which included specifications for chip-based credit cards and point-of-sale (POS) terminals. The new standard required card issuers to issue credit cards with a microprocessor chip, which added an extra layer of security compared to traditional magnetic stripe cards. The chip could generate a unique code for each transaction, making it much more difficult for fraudsters to use stolen card information and nearly impossible to clone and create a counterfeit EMV credit card.
EMV – Adoption in the U.S. and Its Benefits
EMV made its way into the U.S. in 2011, with a mandate requiring businesses to utilize EMV-capable point-of-sale equipment by 2015. Slowly adopted at first, the shift to EMV is now near complete, with 99% of U.S. card payment volume coming from EMV cards. Merchants lag behind, with around 75% of U.S. stores using EMV terminals – that’s 3.5 million merchants – according to Visa. Today, EMV has evolved in several ways to address the changing security landscape and consumer need which include:
- Mobile Payments: EMV has expanded to include mobile payment technology, allowing consumers to make secure, contactless payments using their smartphones, wearables, and other devices.
- Enhanced security features: To address the increasing threat of fraud and data breaches, EMV has introduced enhanced security features such as dynamic authentication, chip-and-pin, and chip-and-signature. These features add an extra layer of security to transactions and make it more difficult for fraudsters to steal card information.
- Contactless payments: The rise of contactless payments has resulted in the introduction of contactless cards and terminals. These cards and terminals use near-field communication (NFC) technology to allow for fast and secure transactions without the need for physical contact.
- Global acceptance: As EMV has become more widespread, it has become a global standard for card payments. This has made it easier for consumers to use their cards when traveling, as well as for merchants to accept card payments from customers around the world.
The adoption of the EMV standard has been gradual and has taken many years, but it has now become the dominant standard for card-present transactions worldwide. This has greatly reduced the risk of fraud and improved the overall security of the payment card industry.
E-commerce Fraud – Still Present with EMV
Since its adoption, EMV has helped to reduce card-present – or counterfeit – fraud. However, consumer spending has shifted online and as a result, E-commerce sales have soared – creating a breeding ground of opportunity for fraudsters.
By the end of 2022, U.S. E-commerce sales reached the $1 trillion mark for the first time. By 2025, e-commerce sales are predicted to make up nearly twenty-four percent of total retail sales in the U.S., an eleven percent increase since 2019. It’s no surprise that with E-commerce growth, card-not present (CNP) fraud – E-commerce fraud – has also increased. Juniper Research’s recent study shows that global e-commerce fraud loss was estimated to reach over $41 billion globally by the end of 2022, and will reach $48 billion by the end of 2023, a sixteen percent increase YoY.
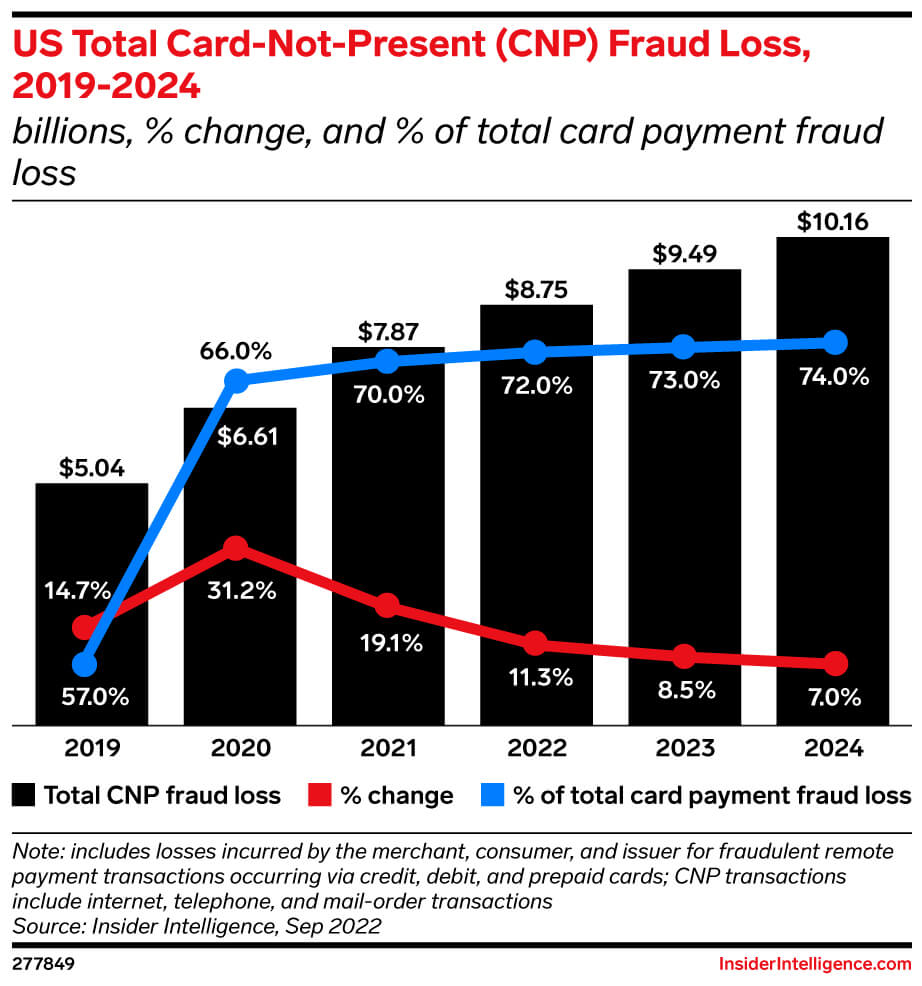
Growth in card fraud losses is slowing annually, but with totals set to reach $13.73 billion by 2024, stakeholders aren’t in the clear: Card-not-present (CNP) fraud will continue to skyrocket as fraudsters see an opportunity online and ramp up attacks to seize it. By 2024, CNP fraud will make up 74% of fraud – up from 57.0% pre-pandemic in 2019—creating new prevention challenges, especially for merchants, who are more liable than other parties for this type of fraud. That means issuers and merchants need to rethink prevention strategies.
EMV – It’s Not Enough Protection Against E-Commerce Fraud
EMV has been effective for reducing card-present fraud, protecting card data at the point of sale (POS) terminal. But once the card data is transmitted to the acquiring bank or payment processor, it becomes vulnerable to theft. Why? EMV chip does not provide any encryption for the credit card primary account number (PAN), expiration date, or cardholder name: three sensitive data elements classified as cardholder data and required to be protected according to PCI DSS.
As E-commerce continues to grow, online merchants will continue to be the target of fraud attacks. Fraudsters are always on the lookout for vulnerabilities within a merchant’s network with the goal of stealing consumer payment data. Additional technology is needed to protect sensitive data.
P2PE and Tokenization – A Holistic Solution
The best data protection is to render the data useless in the event of a data breach. P2PE (Point-to-Point Encryption) and tokenization are two security measures that encrypt and mask sensitive data, ensuring that it never travels through a system or network as clear text, where it could be accessible in the event of a data breach.
Point-to-point encryption (P2PE) protects sensitive data from theft by encrypting the data from the point of capture (such as a POS terminal) all the way to the acquiring bank or payment processor. With P2PE, the data is encrypted before it leaves the POS terminal, making it unreadable to anyone who intercepts the data.
Tokenization, on the other hand, is a process of replacing sensitive information with a unique identifier, or “token”. The token serves as a placeholder for the sensitive information and can be used for transactions without exposing the original data. Tokens cannot be used to derive the original data and so if the tokens are stolen, they are useless to the attacker.
By combining P2PE and tokenization, payment systems can add multiple layers of security to protect sensitive information and prevent e-commerce fraud. For example, P2PE can be used to encrypt sensitive data from the payment terminal to the secure server, and then tokenization can be used to replace the encrypted data with a token for subsequent transactions. This makes it much more difficult for fraudsters to access sensitive information and use it for illegal purposes.
At Bluefin, we are a strong proponent for the holistic payment security approach but feel that to really devalue the data and make it useless to hackers, enterprises and merchants should not handle any clear-text card data.
Bluefin’s PCI-validated P2PE and ShieldConex® tokenization solutions devalue data with encryption and tokenization, which literally makes your customers’ payment information unusable on the Dark Web.