Meet the world’s top PCI-validated point-to-point encryption (P2PE) solution
Bluefin’s encryption solutions secure omnichannel, point-of-sale payments – whether contactless, face-to-face, mobile, call center or unattended. How? We protect POS payment data with the gold standard of encryption, PCI-validated point-to-point encryption (P2PE), and online payments and ACH account data with ShieldConex® encrypted tokenization, removing clear-text cardholder data from your system.
And we offer the most flexibility of any security provider, with solutions available through Bluefin’s products or our global partner network.
Secure Payment P2PE Solutions
Resilient,
Seamless and Flexible Encryption
There are many payment encryption products on the market but only those solutions validated by the PCI SSC have met rigorous standards for encryption, decryption, key management and chain of custody. With Bluefin’s PCI-validated P2PE solutions, payment data is immediately encrypted upon tap, dip, swipe, or key entry in a P2PE certified device, with encryption being done outside of the merchant environment by Bluefin.
And as the first PCI-validated provider of a P2PE solution in 2014, we lead the way – with over 100 P2PE devices, 300 global partners, and the only 100% online portal for chain of custody management, the P2PE Manager®.
Less time meeting compliance and patching holes. More time building your enterprise.
PCI Scope Reduction
Reduce your PCI scope and annual attestation to a PCI P2PE self-assessment questionnaire (SAQ), with just 33 questions.
Cost Savings
Save time and money on security environments, including penetration testing, employee overhead and firewalls.
Brand Protection
Data breaches that expose consumer data damage the brand, lower consumer confidence and can cost millions.
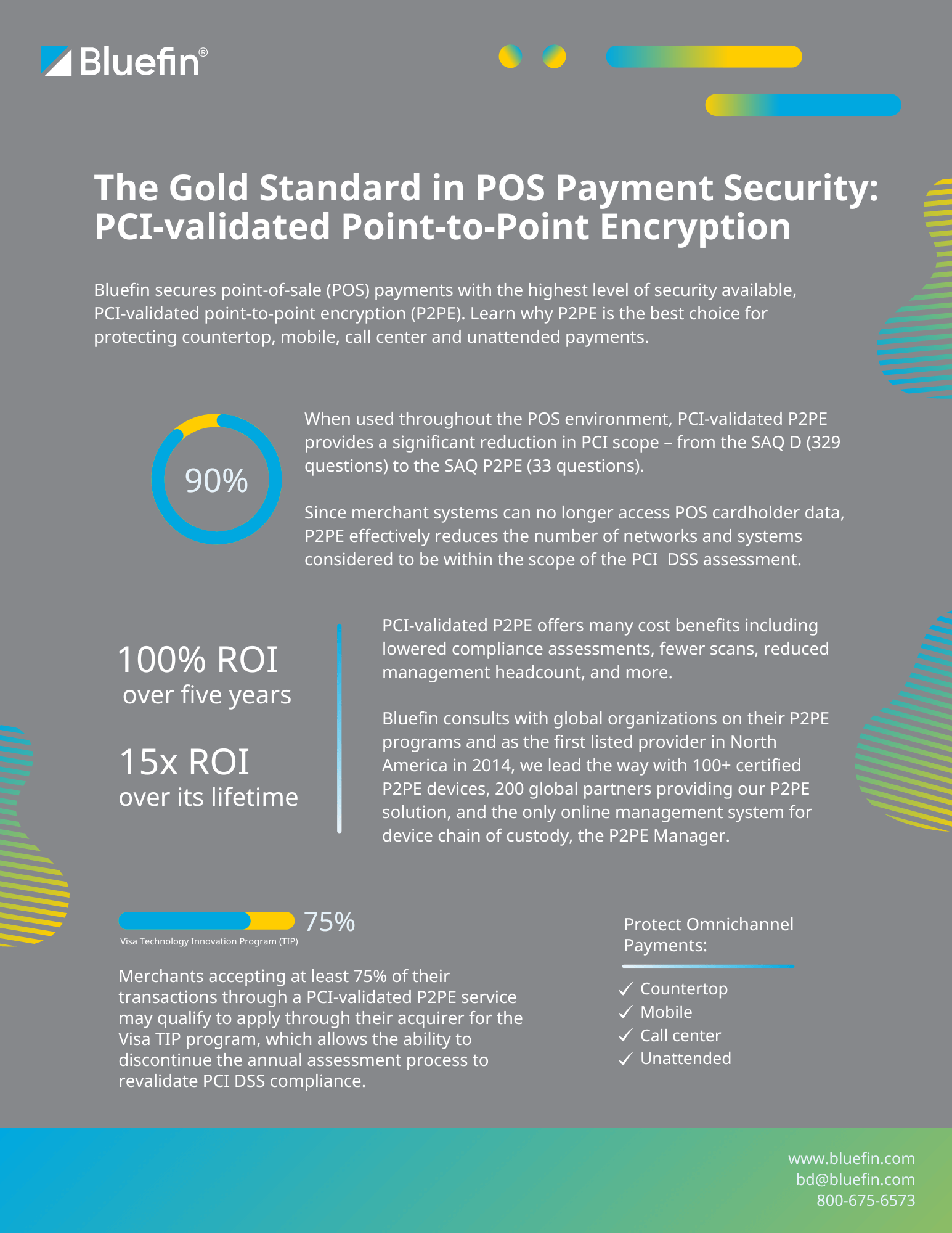
The Gold Standard in POS Payment Security:
PCI-validated Point-to-Point Encryption
Bluefin secures point-of-sale (POS) payments with the highest level of security available, PCI-validated point-to-point encryption (P2PE). Learn why P2PE is the best choice for protecting countertop, mobile, call center and unattended payments.
Get PCI P2PE for your organization
Contact us
"*" indicates required fields