For as long as we’ve been spending money, thieves have invented new ways to snatch their unfair share of the wealth. Just as checks replaced cash and cards replaced checks, EMV-chip card technology was purported to be the next evolution in consumer fraud protection.
Despite such security efforts, recent skimming incidents at major retailers like Walmart and Safeway reflect the rise in sophisticated new technology designed to circumvent EMV and steal consumer data. From overlays to periscope skimmers to shimmers, here are the newest, most advanced ways thieves are targeting financial data.
Overlays
One of the most common forms of credit card skimming, overlays are physical casings placed on top of credit card terminals in self-checkout lanes at gas stations, grocery stores and major retailers. Equipped with Bluetooth technology, these devices allow sneaky thieves to swipe data and PINs from up to 300 feet away.
Overlays have been widely used on Ingenico iSC250 credit card terminals across the country, with notable incidents occurring at Walmarts in Virginia and Kentucky. Retailing on the black market for $200 to $300, the overlays can even store card numbers until thieves are ready to upload their cache of stolen data.
With a little knowledge, anyone can spot the differences between real card readers and fake ones. Since they must be wider than the target device, overlays will appear larger than the actual POS terminal. Other features to look out for include a lack of natural backlighting on the keypad and the absence of a stylus anchored to the side of the device.
Periscope Skimmers
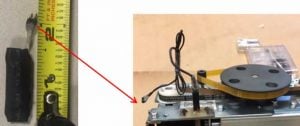
While overlays are relatively easy to detect, it is nearly impossible to look at a device and tell if it has been outfitted with a periscope skimmer. Overlay skimmers are installed on top of an existing ATM’s card slot, allowing for easy instillation and retrieval, but many ATMs are now designed to prevent this kind of fraud.
Representing a dangerous evolution in data theft, periscope skimmers are installed inside an ATM, connecting to the motorized card reader and a circuit board that transfers cardholder data for transaction processing.
While periscope skimmers require a physical key, or “top-hat” entry, to access the ATM’s internal circuits, once installed, these dangerous machines can run for 14 days before the battery runs out, collecting up to 32,000 card numbers. The only significant sign of a periscope reader is a wire extending from the periscope probe to the skimming control device that stores the data. These new kinds of skimmers are thought to be a reaction to the success of third-party anti-skimming technology that prevents skimmers from being placed outside an ATM.
Considered a reaction to the success of ATM technology designed to prevent external overlays, periscope skimmers were discovered in Connecticut and Pennsylvania in the fall of 2016. The installed devices were not equipped with hidden cameras or other ways to capture PINs, so many security experts view these devices as potential prototypes — an ominous sign of things to come.
Shimmers
Security experts are sounding the alarm on a sophisticated new form of credit card fraud designed to take advantage of new chip-card technology. Most skimming devices record the unencrypted data stored on a card’s magnetic stripe, but “shimming” represents an entirely new way to steal this valuable data.
Designed to bilk consumers out of millions, a “shim” is inserted into the mouth of a card reader, sitting between the chip on the card and the chip reader in the ATM’s POS device — reading and recording data from chip-enabled credit and debit cards.
Spotted in Mexico and Canada, this new kind of fraud cannot be used to fabricate counterfeit chip cards, but it can still be used to clone and create a magnetic stripe card. While data stored on a magnetic stripe is also replicated inside chip-enabled cards, integrated circuit card verification (iCVV) protects chip cards against the copying of magnetic stripe data.
Shimmers exist because many banks have yet to implement the EMV chip card standard, which requires bankcard issuers to check the CVV when authorizing a transaction. Card shimming is not a flaw in the chip card or the ATM, and banks can run a quick check to see if a card inserted into an ATM is a counterfeit magnetic stripe encoded with stolen chip card data. The rise in these threats indicates that many thieves have identified banks and ATMs that may be particularly vulnerable to shimmer attacks.
Put the Skids on Skimming
Despite the vulnerabilities surrounding cards equipped with magnetic stripes, this antiquated technology will persist for quite some time since consumers are familiar with the technology, and stripes remain an integral part of the way ATMs work.
Instead of wishing for the demise of the magnetic stripe, consumers should learn how to spot overlays and protect their data from looming cameras by placing a hand over pin-pads when keying their PIN number. Without access to a PIN, thieves cannot drain a debit account using a cloned card at an ATM. Other expert suggestions including avoid visiting ATMs on weekends, when devices go uninspected for longer periods of time, and avoid shim, overlay and periscope attacks by sticking to ATMs that are physically installed in a wall or at a bank.
As payment methods continue to evolve and adapt to the way we live now, thieves will be close behind, ready to exploit any available loopholes.