Verizon has released their 13th annual Data Breach Investigation Report (DBIR), analyzing 3,950 confirmed breaches in 2019. What do this year’s findings tell us? Threat actors are still up to their old tricks, with hacking involved in 45% of breaches and ransomware rising 2.6% since 2019. 86% of breaches are for financial gain, 43% of breaches used web applications – and large businesses remain the main targets of hackers.
Major Threat Vectors
While many believe that people inside the organization are a bigger threat than those outside of the organization, the DBIR found that threat actors are responsible for 70% of data breaches, and in 55% of those cases organized criminals are the perpetrators. When internal breaches do happen, it is usually due to user error (22%).
There is some good and bad news when it comes to what cybercriminals have been up to. Verizon found that the status of physical breaches has stayed the same, and Misuse, Hacking, Malware, and Social have decreased since last year. Malware has been on a steady decline the last five years; hackers use it in simpler attacks. Another positive that came out of Verizon’s findings is that Social comes via email 96% of the time and click rates are at the lowest they have ever been (3.4%).
 Now the bad news. Ransomware usage continues to rise and it is resulting in the theft of user credentials and personal information being stolen, while also serving as a vehicle for the installation of malware. While Verizon found that ransomware only accounted for 3.5% of the unique malware samples, malware is still a threat with new varieties. Password dumper, which enables fraudsters to get credentials, is the number one malware variety, followed by: Capture App data, and Ransomware. Email and Direct Install are the top vectors, which should not be surprising since they are related to phishing attacks.
Now the bad news. Ransomware usage continues to rise and it is resulting in the theft of user credentials and personal information being stolen, while also serving as a vehicle for the installation of malware. While Verizon found that ransomware only accounted for 3.5% of the unique malware samples, malware is still a threat with new varieties. Password dumper, which enables fraudsters to get credentials, is the number one malware variety, followed by: Capture App data, and Ransomware. Email and Direct Install are the top vectors, which should not be surprising since they are related to phishing attacks.
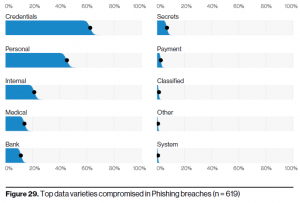
“While credentials are by far the most common attribute compromised in phishing breaches,” says the report, “Phishing has been (and still remains) a fruitful method for attackers.”
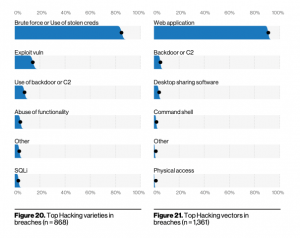
Nearly half of the breaches studied (45%) involved hacking. Credential theft is what is driving Hacking and breaches in general. One reason there is an increase in actors wanting credentials is the increase of the information stored in the cloud, which can include email accounts and business process.
Top Industries Affected
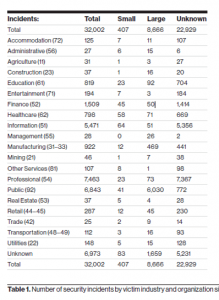
DBIR also takes a deep dive into industry specific data breaches, followed by the nine incident patterns most commonly associated with the reported data breaches. The report explored 157,525 incidents. Healthcare topped the list with 521 breaches, followed by the financial sector (448), and information (360).
DBIR 2020 – Conclusion
 This year’s report contains valuable information and the authors hope that after reading this document, companies will use it to make their organization’s cybersecurity decisions differently and more proactively.
This year’s report contains valuable information and the authors hope that after reading this document, companies will use it to make their organization’s cybersecurity decisions differently and more proactively.
Bluefin is a staunch believer in a proactive security approach to protect data, which is why we teamed up with Verizon Enterprise Solutions in 2019 to issue our white paper on the Value of P2PE in POI and POS environments. The paper, authored by Verizon’s Ciske van Oosten, overviews the POI/POS threat landscape and details how criminals obtain access to cardholder data (CHD), while discussing the evolution of P2PE, the differences between certified and non-certified encryption solutions, benefits of PCI-validated P2PE solutions in POI environments, including compliance management and scope reduction, and the roles of tokenization, EMV and P2PE in protecting data. The best way to mitigate the effect of a data breach is a defense-in-depth security strategy that involves devaluing sensitive personal and payment data.
To learn more about our security solutions, contact us today.